IPSec遂道配置参数解析Word文档格式.docx
《IPSec遂道配置参数解析Word文档格式.docx》由会员分享,可在线阅读,更多相关《IPSec遂道配置参数解析Word文档格式.docx(26页珍藏版)》请在冰豆网上搜索。
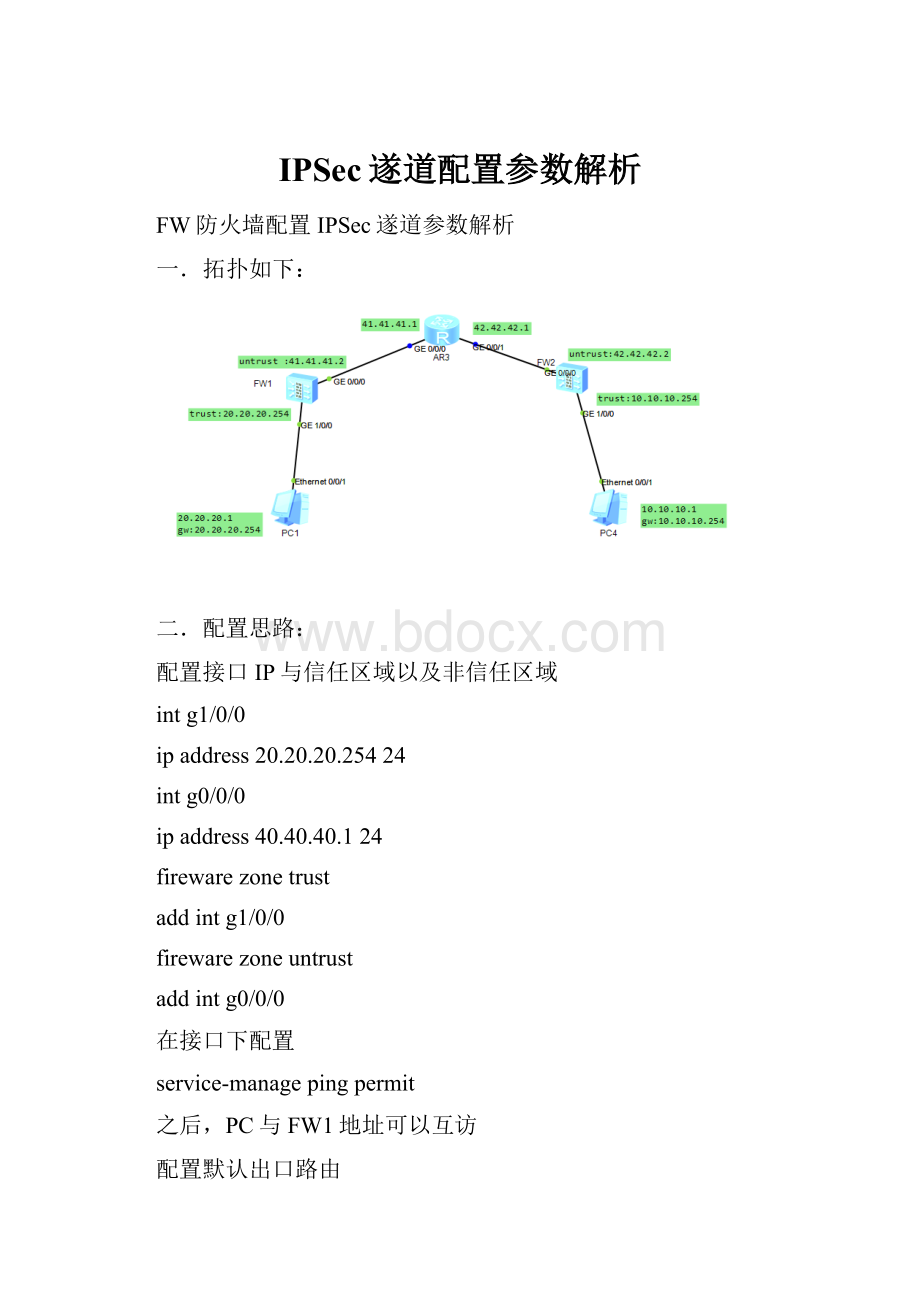
配置IPsecproposal
ipsecproposalmyset(myset_fw1/myset_fw2在不同防火墙上配置不同)
transformesp
espauthentication-algorithmsha1
espencryption-algorithm3des
配置IKEpeer
ikepeerfw(fw2/fw1,同上,在不同防火墙上配置不同)
pre-shared-keyhuawei123(密码,两端必须设置一致)
ike-proposal10
remote-address(配置为对端FW的非信任区IP,42.42.42.2/41.41.41.2,为遂道两侧地址,这边设置为对端地址)
遂道内流量匹配才可以通过,另外一个防火墙流量应该反过来
配置遂道内流量放通策略,并且在对应接口上应用
aclnumber3000
rulepermitipsource20.20.20.00.0.0.255destination10.10.10.00.0.0.255
配置FW上IPsecPolicy
ipsecpolicymymap10isakmp
securityacl3000
ike-peerfw2
tunnellocal(配置为本端FW的非信任区IP,41.41.41.2/42.42.42.2,为遂道两侧地址,这边设置为本端地址)
proposalmyset(myset_fw1/myset_fw2,同上,在不同防火墙上配置不同)
配置应用IPsecpolicy到接口(untrust流量出去的接口)
interfaceg0/0/0
ipsecpolicymymap
配置流量放通策略
下面是FW2上配置数据,分别是
到目标10.10.10.0的流量放通,从10.10.10.0出去流量放通
到目标42.42.42.0的流量放通,从42.42.42.0出去流量放通
FW1上配置数据,应该是
到目标20.20.20.0的流量放通,从20.20.20.0出去流量放通
到目标41.41.41.0的流量放通,从41.41.41.0出去流量放通
[FW2-policy-security]
#
security-policy
rulename20in
destination-zonetrust
destination-address10.10.10.00.0.0.255
actionpermit
rulenametest11
source-address42.42.42.0mask255.255.255.0
rulenametest12
destination-address42.42.42.0mask255.255.255.0
rulename20out
source-zonetrust
source-address10.10.10.0mask255.255.255.0
#return
三.结果验证:
从PC1pingPC4,可达
。
从PC4pingPC1,可达。
抓包分析,可以看到上面PC1与PC4互相ping可达,在FW1--FW2之间抓包,PC1与PC4的IP地址已经隐藏,完全通过加密遂道传输,只能看到遂道两侧地址进行数据交互。
四.完整数据:
<
FW1>
discurrent-configuration
2020-03-3013:
03:
04.390
!
SoftwareVersionV500R005C10SPC300
#
sysnameFW1
l2tpdomainsuffix-separator@
ipsecsha2compatibleenable
undotelnetserverenable
undotelnetipv6serverenable
clocktimezoneUTCadd00:
00:
00
updateschedulelocation-sdbweeklySun22:
05
firewalldefendactiondiscard
bannerenable
user-manageweb-authenticationsecurityport8887
undoprivacy-statementenglish
undoprivacy-statementchinese
page-setting
user-managesecurityversiontlsv1.1tlsv1.2
password-policy
levelhigh
user-managesingle-sign-onad
user-managesingle-sign-ontsm
user-managesingle-sign-onradius
user-manageauto-synconline-user
web-managersecurityversiontlsv1.1tlsv1.2
web-managerenable
web-managersecurityenable
firewalldataplanetomanageplaneapplication-apperceivedefault-actiondrop
undoipslogmergeenable
decodinguri-cachedisable
updatescheduleips-sdbdaily05:
37
updatescheduleav-sdbdaily05:
updateschedulesa-sdbdaily05:
updateschedulecncdaily05:
updateschedulefile-reputationdaily05:
ipvpn-instancedefault
ipv4-family
time-rangeworktime
period-range08:
00to18:
00working-day
rule5permitipsource20.20.20.00.0.0.255destination10.10.10.00.0.0.255
ipsecproposalmyset_fw1
espauthentication-algorithmsha1
espencryption-algorithm3des
ikeproposaldefault
encryption-algorithmaes-256aes-192aes-128
dhgroup14
authentication-algorithmsha2-512sha2-384sha2-256
authentication-methodpre-share
integrity-algorithmhmac-sha2-256
prfhmac-sha2-256
encryption-algorithm3des
dhgroup2
authentication-algorithmsha1
ikepeerfw2
pre-shared-key%^%#]#ZG'
w_qoVDFBV)u$D>
YU)u'
=*CX~XO-gSV\eGz!
%^%#
ike-proposal10
remote-address42.42.42.2
securityacl3000
ike-peerfw2
proposalmyset_fw1
tunnellocal41.41.41.2
aaa
authentication-schemedefault
authentication-schemeadmin_local
authentication-schemeadmin_radius_local
authentication-schemeadmin_hwtacacs_local
authentication-schemeadmin_ad_local
authentication-schemeadmin_ldap_local
authentication-schemeadmin_radius
authentication-schemeadmin_hwtacacs
authentication-schemeadmin_ad
authorization-schemedefault
accounting-schemedefault
domaindefault
service-typeinternetaccessssl-vpnl2tpike
internet-accessmodepassword
referenceusercurrent-domain
manager-useraudit-admin
passwordcipher@%@%jzvO,YbEn-I6AQ8(vHYBT7cC-/yn<
d.8i7o,sV~o##J47cFT@%@%
service-typewebterminal
level15
manager-userapi-admin
passwordcipher@%@%UcRX<
t1eSN7&
+C/boP*MHGKc]1nK'
a0fL@II~1O\(JETGKfH@%@%
manager-useradmin
passwordcipher@%@%Ed#lS9$SO~k5hyTi5js(viI}Z{3FXV,ZePW}%$V9[qSAiI#v@%@%
rolesystem-admin
roledevice-admin
roledevice-admin(monitor)
roleaudit-admin
bindmanager-useraudit-adminroleaudit-admin
bindmanager-useradminrolesystem-admin
l2tp-groupdefault-lns
interfaceGigabitEthernet0/0/0
undoshutdown
ipaddress41.41.41.2255.255.255.0
service-managepingpermit
ipsecpolicymymap
interfaceGigabitEthernet1/0/0
ipaddress20.20.20.254255.255.255.0
interfaceGigabitEthernet1/0/1
interfaceGigabitEthernet1/0/2
interfaceGigabitEthernet1/0/3
interfaceGigabitEthernet1/0/4
interfaceGigabitEthernet1/0/5
interfaceGigabitEthernet1/0/6
interfaceVirtual-if0
interfaceNULL0
firewallzonelocal
setpriority100
firewallzonetrust
setpriority85
addinterfaceGigabitEthernet1/0/0
firewallzoneuntrust
setpriority5
addinterfaceGigabitEthernet0/0/0
firewallzonedmz
setpriority50
iproute-static0.0.0.00.0.0.041.41.41.1
undosshservercompatible-ssh1xenable
sshauthentication-typedefaultpassword
sshservercipheraes256_ctraes128_ctr
sshserverhmacsha2_256sha1
sshclientcipheraes256_ctraes128_ctr
sshclienthmacsha2_256sha1
firewalldetectftp
user-interfacecon0
authentication-modeaaa
user-interfacevty04
protocolinboundssh
user-interfacevty1620
pkirealmdefault
sa
location
multi-linkif
modeproportion-of-weight
right-managerserver-group
device-classification
device-grouppc
device-groupmobile-terminal
device-groupundefined-group
user-manageserver-synctsm
rulename10out
source-address20.20.20.00.0.0.255
rulename10in
destination-address20.20.20.00.0.0.255
rulenametest1
destination-address41.41.41.0mask255.255.255.0
rulenametest2
source-address41.41.41.0mask255.255.255.0
auth-policy
traffic-policy
policy-based-route
nat-policy
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
return
FW2>
08:
35.340
sysnameFW2
updateschedulelocation-sdbweeklySun05:
09
updatescheduleips-sdbdaily06:
18
updatescheduleav-sdbdaily06:
updateschedulesa-sdbdaily06:
updateschedulecncdaily06:
updateschedulefile-reputationdaily06:
rule5permitipsource10.10.10.00.0.0.255destination20.20.20.00.0.0.255
ipsecproposalmyset_fw2
ikepeerfw1
pre-shared-key%^%#IUDj"
*:
Xs=;
eNi~P21R4fO2$B4t:
~Uhe^2#Q#:
+(%^%#
remote-address41.41.41.2
ike-peerfw1
proposalmyset_fw2
tunnellocal42.42.42.2