在思科Pix防火墙和NetScreen防火墙间配置LANtoLAN.docx
《在思科Pix防火墙和NetScreen防火墙间配置LANtoLAN.docx》由会员分享,可在线阅读,更多相关《在思科Pix防火墙和NetScreen防火墙间配置LANtoLAN.docx(21页珍藏版)》请在冰豆网上搜索。
在思科Pix防火墙和NetScreen防火墙间配置LANtoLAN
在思科Pix防火墙和NetScreen防火墙间配置LAN-to-LANVPN
亚威科技
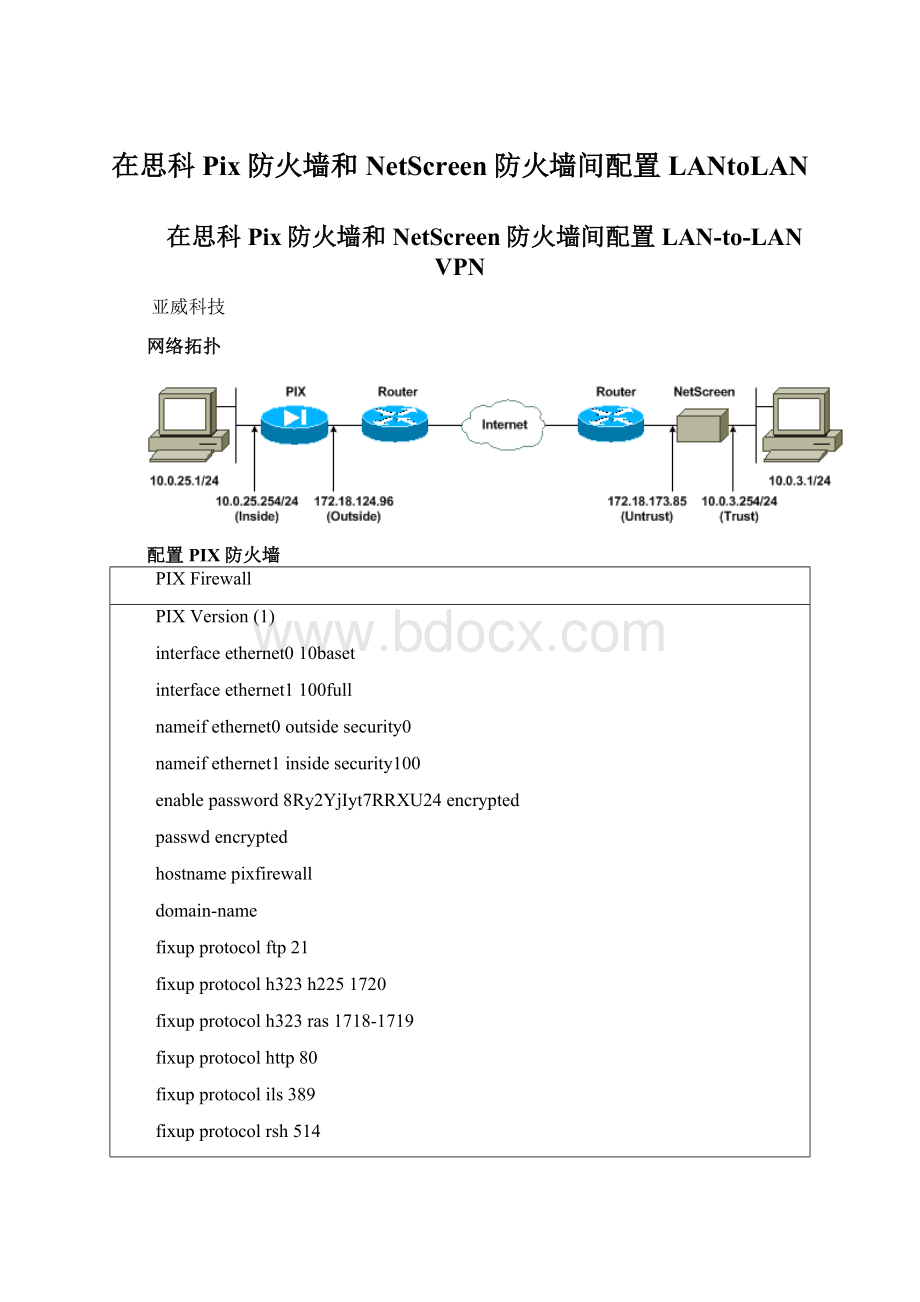
网络拓扑
配置PIX防火墙
PIXFirewall
PIXVersion
(1)
interfaceethernet010baset
interfaceethernet1100full
nameifethernet0outsidesecurity0
nameifethernet1insidesecurity100
enablepassword8Ry2YjIyt7RRXU24encrypted
passwdencrypted
hostnamepixfirewall
domain-name
fixupprotocolftp21
fixupprotocolh323h2251720
fixupprotocolh323ras1718-1719
fixupprotocolhttp80
fixupprotocolils389
fixupprotocolrsh514
fixupprotocolrtsp554
fixupprotocolsip5060
fixupprotocolsipudp5060
fixupprotocolskinny2000
fixupprotocolsmtp25
fixupprotocolsqlnet1521
names
!
---Accesscontrollist(ACL)forinterestingtraffictobeencryptedand
!
---tobypasstheNetworkAddressTranslation(NAT)process
access-listnonatpermitiplines24
loggingon
loggingtimestamp
loggingbuffereddebugging
icmppermitanyinside
mtuoutside1500
mtuinside1500
!
---IPaddressesontheinterfaces
ipaddressoutsideaddressinsideauditinfoactionalarm
ipauditattackactionalarm
pdmlogginginformational100
pdmhistoryenable
arptimeout14400
global(outside)1interface
!
---BypassofNATforIPSecinterestinginsidenetworktraffic
nat(inside)0access-listnonat
nat(inside)100
!
---DefaultgatewaytotheInternet
routeoutside1
timeoutxlate0:
05:
00
timeoutconn1:
00:
00half-closed0:
10:
00udp0:
02:
00rpc0:
10:
00h2251:
00:
00
timeouth3230:
05:
00mgcp0:
05:
00sip0:
30:
00sip_media0:
02:
00
timeoutuauth0:
05:
00absolute
aaa-serverTACACS+protocoltacacs+
aaa-serverRADIUSprotocolradius
aaa-serverLOCALprotocollocal
httpinside
nosnmp-serverlocation
nosnmp-servercontact
snmp-servercommunitypublic
nosnmp-serverenabletraps
floodguardenable
!
---ThiscommandavoidsappliedACLsorconduitsonencryptedpackets
sysoptconnectionpermit-ipsec
!
---ConfigurationofIPSecPhase2
cryptoipsectransform-setmytransesp-3desesp-sha-hmac
cryptomapmymap10ipsec-isakmp
cryptomapmymap10matchaddressnonat
cryptomapmymap10setpfsgroup2
cryptomapmymap10setpeermapmymap10settransform-setmytrans
cryptomapmymapinterfaceoutside
!
---ConfigurationofIPSecPhase1
isakmpenableoutside
!
---InternetKeyExchange(IKE)pre-sharedkey
!
---thatthepeerswillusetoauthenticate
isakmpkeytestmeaddressnetmaskidentityaddress
isakmppolicy10authenticationpre-share
isakmppolicy10encryption3des
isakmppolicy10hashsha
isakmppolicy10group2
isakmppolicy10lifetime86400
telnettimeout5
sshtimeout5
consoletimeout0
dhcpdlease3600
dhcpdping_timeout750
terminalwidth80
配置NetScreen防火墙
FollowthestepsbelowtoconfiguretheNetScreenFirewall.
GotoLists>Address,clicktheTrustedtab,andclickNewAddress.
AddtheNetscreeninternalnetworkthatwillbeencryptedonthetunnel,thenclickOK.
Note:
EnsurethattheTrustoptionisselected.
Theexamplebelowusesnetworkwithamaskof
toLists>Address,clicktheUntrustedtab,andclickNewAddress.
AddtheremotenetworkthatNetScreenFirewallwillusewhenencryptingpackets,thenclickOK.
Theexamplebelowusesnetworkwithamaskof
configuretheVPNgateway(Phase1andPhase2IPSecpolicies),gotoNetwork>VPN,selecttheGatewaytab,andclickNewRemoteTunnelGateway.
UsetheIPaddressofthePIX'soutsideinterfacetoterminatethetunnel,andconfigurethePhase1IKEoptionstobind.ClickOKwhenyouarefinished.
Thisexampleusesthefollowingfieldsandvalues.
GatewayName:
To501
StaticIPAddress:
Main(IDProtection)
PresharedKey:
“testme”
Phase1proposal:
pre-g2-3des-sha
Whenyouhavesuccessfullycreatedtheremotetunnelgateway,youshouldseeascreensimilartothefollowingexample.
ToconfigureProposal1,selecttheP1Proposaltab,andthenclickNewPhase1Proposal.
EntertheconfigurationinformationforthePhase1Proposal,andthenclickOK.
ThisexampleusesthefollowingfieldsandvaluesPhase1exchange.
Name:
ToPix501
Authentication:
Preshare
DHGroup:
Group2
Encryption:
3DES-CBC
Hash:
SHA-1
Lifetime:
3600Sec.
WhenyouhavesuccessfullyaddedPhase1totheNetScreenconfiguration,youshouldseeascreensimilartothefollowingexample.
ToconfigurePhase2,selecttheP2Proposaltab,andthenclickNewPhase2Proposal.
EntertheconfigurationinformationforthePhase2Proposal,andthenclickOK.
ThisexampleusesthefollowingfieldsandvaluesforPhase2exchange.
Name:
ToPix501
PerfectForwardSecrecy:
DH-2(1024bits)
EncryptionAlgorithm:
3DES-CBC
AuthenticationAlgorithm:
SHA-1
Lifetime:
26400Sec
WhenyouhavesuccessfullyaddedPhase2totheNetScreenconfiguration,youshouldseeascreensimilartothefollowingexample.
TocreateandconfigureAutoKeysIKE,selecttheAutoKeyIKEtab,andthenclickNewAutoKeyIKEEntry.
EntertheconfigurationinformationforAutoKeyIKE,andthenclickOK.
ThisexampleusesthefollowingfieldsandvaluesforAutoKeyIKE.
Name:
VPN-1
RemoteGatewayTunnelName:
To501
(ThiswaspreviouslycreatedontheGatewaytab.)
Phase2Proposal:
ToPix501
(ThiswaspreviouslycreatedontheP2Proposaltab.)
VPNMonitor:
Enable
(ThisenablestheNetScreendevicetosetSimpleNetworkManagementProtocol[SNMP]trapstomonitortheconditionoftheVPNMonitor.)
WhenyouhavesuccessfullyconfiguredtheVPN-1rule,youshouldseeascreensimilartothefollowingexample.
ToconfiguretherulesthatallowencryptionoftheIPSectraffic,gotoNetwork>Policy,selecttheOutgoingtab,andclickNewPolicy.
Entertheconfigurationinformationforthepolicy,andthenclickOK.
Thisexampleusesthefollowingfieldsandvaluesforthepolicy.TheNamefieldisoptionalandisnotusedinthisexample.
SourceAddress:
InsideNetwork
(ThiswaspreviouslydefinedontheTrustedtab.)
DestinationAddress:
RemoteNetwork
(ThiswaspreviouslydefinedundertheUntrustedtab.)
Service:
Any
Action:
Tunnel
VPNTunnel:
VPN-1
(ThiswaspreviouslydefinedastheVPNtunnelontheAutoKeyIKEtab.)
ModifymatchingincomingVPNpolicy:
Checked
(ThisoptionautomaticallycreatesaninboundrulethatmatchestheoutsidenetworkVPNtraffic.)
Whenyouhaveaddedthepolicy,ensurethattheoutboundVPNruleisfirstinthelistofpolicies.(TherulethatwascreatedautomaticallyforinboundtrafficisontheIncomingtab.)
Ifyouneedtochangetheorderofthepolicies,followthesesteps.
ClicktheOutgoingtab.
ClickthecirculararrowsintheConfigurecolumntodisplaytheMovePolicyMicrowindow.
ChangetheorderofthepoliciessothattheVPNpolicyisabovepolicyID0(sothattheVPNpolicyisatthetopofthelist).
YoucanviewtheruleforinboundtrafficbyclickingontheIncomingtab.
验证配置
ping-Diagnosesbasicnetworkconnectivity.
showcryptoipsecsa-ShowsthePhase2securityassociations.
showcryptoisakmpsa-ShowsthePhase1securityassociations.
验证示例
Sampleoutputfrompingandshowcommandsisshowbelow.
ThispingwasinitiatedfromahostbehindtheNetScreenFirewall.
C:
\>ping-t
Requesttimedout.
Requesttimedout.
Replyfrombytes=32time<105msTTL=128
Replyfrombytes=32time<114msTTL=128
Replyfrombytes=32time<106msTTL=128
Replyfrombytes=32time<121msTTL=128
Replyfrombytes=32time<110msTTL=128
Replyfrombytes=32time<116msTTL=128
Replyfrombytes=32time<109msTTL=128
Replyfrombytes=32time<110msTTL=128
Replyfrombytes=32time<118msTTL=128
Outputfromtheshowcryptoipsecsacommandisshownbelow.
pixfirewall(config)#showcryptoipsecsa
interface:
outside
Cryptomaptag:
mymap,localaddr.localident(addr/mask/prot/port):
remoteident(addr/mask/prot/port):
current_peer:
PERMIT,flags={origin_is_acl,}
#pktsencaps:
11,#pktsencrypt:
11,#pktsdigest11
#pktsdecaps:
11,#pktsdecrypt:
13,#pktsverify13
#pktscompressed:
0,#pktsdecompressed:
0
#pktsnotcompressed:
0,#pktscompr.failed:
0,
#pktsdecompressfailed:
0,#senderrors0,#recverrors1
localcryptoendpt.:
remotecryptoendpt.:
pathmtu1500,ipsecoverhead56,mediamtu1500
currentoutboundspi:
f0f376eb
inboundespsas:
spi:
0x1225ce5c(8)
transform:
esp-3desesp-sha-hmac,
inusesettings={Tunnel,}
slot:
0,connid:
3,cryptomap:
mymap
satiming:
remainingkeylifetime(k/sec):
(4607974/24637)
IVsize:
8bytes
replaydetectionsupport:
Y
inboundahsas:
inboundpcpsas:
outboundespsas:
spi:
0xf0f376eb(31)
transform:
esp-3desesp-sha-hmac,
inusesettings={Tunnel,}
slot:
0,connid:
4,cryptomap:
mymap
satiming:
remainingkeylifetime(k/sec):
(4607999/24628)
IVsize:
8bytes
replaydetectionsupport:
Y
outboundahsas:
outboundpcpsas:
Outputfromtheshowcryptoisakmpsacommandisshownbelow.
pixfirewall(config)#showcryptoisakmpsa
Total:
1
Embryonic:
0
dstsrcstatependingcreated
QM_IDLE01
Troubleshoot
Thissectionprovidesinformationyoucanusetotroubleshootyourconfiguration.
调试命令
debugcryptoengine-Displaysmessagesaboutcryptoengines.
debugcryptoipsec-DisplaysinformationaboutIPSecevents.
debugcryptoisakmp-DisplaysmessagesaboutIKEevents.
调试示例
SampledebugoutputfromthePIXFirewallisshownbelow.
debugcryptoengine
debugcryptoipsec
debugcryptoisakmp
crypto_isakmp_process_block:
src:
dest:
spt:
500dpt:
500
OAK_MMexchange
ISAKMP(0):
processingSApayload.messageID=0
ISAKMP(0):
CheckingISAKMPtransform1againstpriority10policy
ISAKMP:
encryption3DES-CBC
ISAKMP:
hashSHA
ISAKMP:
defaultgroup2
ISAKMP:
authpre-share
ISAKMP:
lifetypeinseconds
ISAKMP:
lifeduration(basic)of28800
ISAKMP(0):
attsareacceptable.Nextpayloadis0
ISAKMP(0):
proc