Encryption and VPN TechnologyWord文档格式.docx
《Encryption and VPN TechnologyWord文档格式.docx》由会员分享,可在线阅读,更多相关《Encryption and VPN TechnologyWord文档格式.docx(30页珍藏版)》请在冰豆网上搜索。
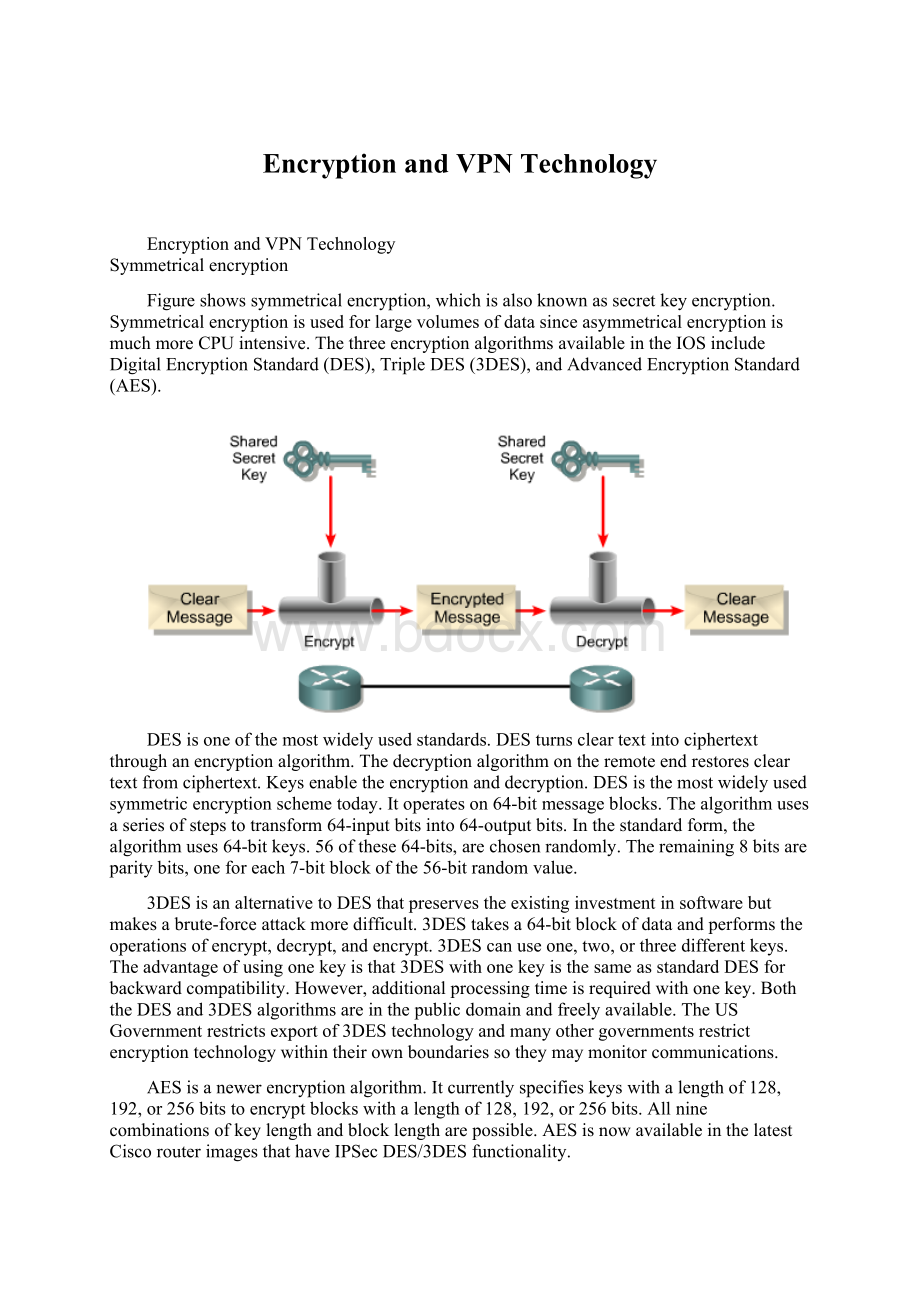
EncryptionandVPNTechnology@#@ @#@@#@EncryptionandVPNTechnology@#@Symmetricalencryption@#@Figureshowssymmetricalencryption,whichisalsoknownassecretkeyencryption.SymmetricalencryptionisusedforlargevolumesofdatasinceasymmetricalencryptionismuchmoreCPUintensive.ThethreeencryptionalgorithmsavailableintheIOSincludeDigitalEncryptionStandard(DES),TripleDES(3DES),andAdvancedEncryptionStandard(AES).@#@DESisoneofthemostwidelyusedstandards.DESturnscleartextintociphertextthroughanencryptionalgorithm.Thedecryptionalgorithmontheremoteendrestorescleartextfromciphertext.Keysenabletheencryptionanddecryption.DESisthemostwidelyusedsymmetricencryptionschemetoday.Itoperateson64-bitmessageblocks.Thealgorithmusesaseriesofstepstotransform64-inputbitsinto64-outputbits.Inthestandardform,thealgorithmuses64-bitkeys.56ofthese64-bits,arechosenrandomly.Theremaining8bitsareparitybits,oneforeach7-bitblockofthe56-bitrandomvalue.@#@3DESisanalternativetoDESthatpreservestheexistinginvestmentinsoftwarebutmakesabrute-forceattackmoredifficult.3DEStakesa64-bitblockofdataandperformstheoperationsofencrypt,decrypt,andencrypt.3DEScanuseone,two,orthreedifferentkeys.Theadvantageofusingonekeyisthat3DESwithonekeyisthesameasstandardDESforbackwardcompatibility.However,additionalprocessingtimeisrequiredwithonekey.BoththeDESand3DESalgorithmsareinthepublicdomainandfreelyavailable.TheUSGovernmentrestrictsexportof3DEStechnologyandmanyothergovernmentsrestrictencryptiontechnologywithintheirownboundariessotheymaymonitorcommunications.@#@AESisanewerencryptionalgorithm.Itcurrentlyspecifieskeyswithalengthof128,192,or256bitstoencryptblockswithalengthof128,192,or256bits.Allninecombinationsofkeylengthandblocklengtharepossible.AESisnowavailableinthelatestCiscorouterimagesthathaveIPSecDES/3DESfunctionality.@#@Themostimportantfeatureofacryptographicalgorithmisitssecurityagainstbeingcompromised.Thesecurityofacryptosystem,orthedegreeofdifficultyforanattackertodeterminethecontentsoftheciphertext,isafunctionofafewvariables.Inmostprotocols,thecornerstonetosecurityliesinthesecrecyofthekeyusedtoencryptdata.Symmetricencryptionalgorithmsarebuiltsothatitisextremelydifficultforanyonetodeterminethecleartextwithouthavingthiskey.Inanycryptosystem,greatlengthsaretakentoprotectthesecrecyoftheencryptionkey.@#@Asymmetricalencryption@#@Asymmetricencryptionisoftenreferredtoaspublickeyencryption.Itcanuseeitherthesamealgorithm,ordifferentbutcomplementaryalgorithmstoscrambleandunscrambledata.Therequiredpublickeyandaprivatekeyaredifferent,butrelated.Forexample,ifAliceandBobwanttocommunicateusingpublickeyencryption,bothneedapublickeyandprivatekeypair.Alicehastocreateherpublickey/privatekeypair,andBobhastocreatehisownpublickey/privatekeypair.Whencommunicatingwitheachothersecurely,AliceandBobusedifferentkeystoencryptanddecryptdata.@#@Themechanismsusedtogeneratethesepublic/privatekeypairsarecomplex,buttheyresultinthegenerationoftwoverylargerandomnumbers.Oneofwhichbecomesthepublickeyandtheotherbecomestheprivatekey.Becausethesenumbers,aswellastheirproduct,mustadheretostringentmathematicalcriteriatopreservetheuniquenessofeachpublic/privatekeypair,generatingthesenumbersisfairlyprocessorintensive.@#@SomeofthemorecommonpublickeyalgorithmsaretheRivest-Shamir-Adleman(RSA)algorithmandtheElGamalalgorithm.Publickeyencryptionalgorithmsarerarelyusedfordataconfidentialitybecauseoftheirperformanceconstraints.Instead,publickeyencryptionalgorithmsaretypicallyusedinapplicationsinvolvingauthenticationusingdigitalsignaturesandkeymanagement.@#@RSAisthepublickeycryptographicsystemdevelopedbyRonRivest,AdiShamir,andLeonardAdleman.ThetwomethodsareRSAsignaturesandRSAencryption.RSAencryptiongeneratesavalueknownasanonce.Anonceistemporaryrandomstring,whichisgeneratedandcombinedwiththepeerpublickey.Thisismoresecurethanthesharedkeymethodofauthentication.However,itrequiresmoreprocessingpoweranddecreasesthroughputperformance.AnRSAsignatureisthemethodthatusesdigitalcertificates.Thismethodisveryscalableandtypicallyisusedbymediumandlargecorporations.@#@Non-repudiationistheabilitytoproveatransactionoccurred,similartoasignedpackagereceivedfromashippingcompany.Thisisveryimportantinfinancialtransactionsandsimilardatatransactions.RSAsignaturesprovidenon-repudiation.RSAencryptiondoesnotprovidenon-repudiat