路由器IPSecOverGRE典型配置.docx
《路由器IPSecOverGRE典型配置.docx》由会员分享,可在线阅读,更多相关《路由器IPSecOverGRE典型配置.docx(14页珍藏版)》请在冰豆网上搜索。
路由器IPSecOverGRE典型配置
路由器-IPSec-Over-GRE典型配置
路由器-IPSec-Over-GRE典型配置
【需求】
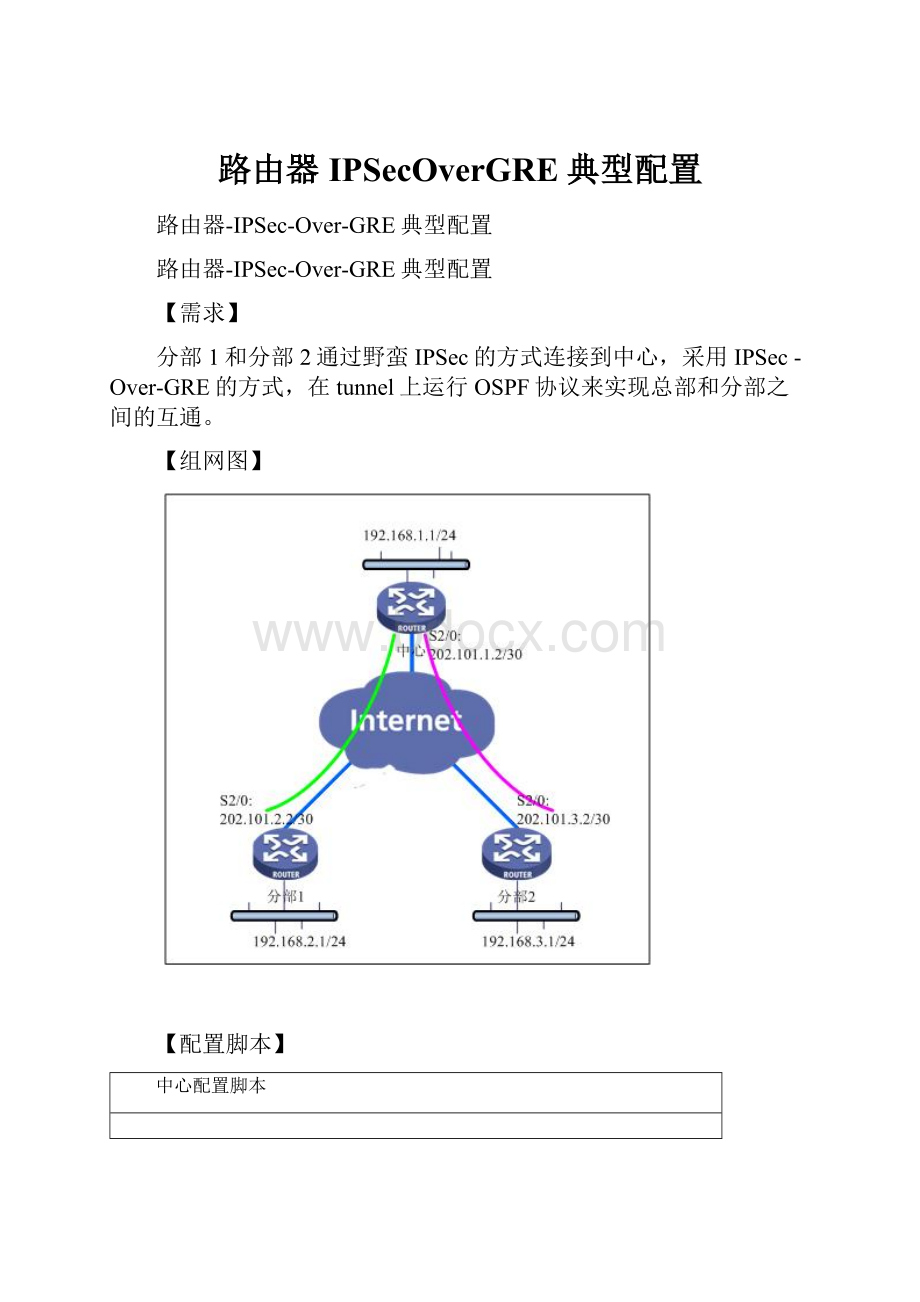
分部1和分部2通过野蛮IPSec的方式连接到中心,采用IPSec-Over-GRE的方式,在tunnel上运行OSPF协议来实现总部和分部之间的互通。
【组网图】
【配置脚本】
中心配置脚本
#
sysnameCenter
#
ikelocal-namecenter /中心ike的local-name为:
center/
#
routerid1.1.1.1
#
radiusschemesystem
#
domainsystem
#
#
iproute-static0.0.0.00.0.0.0202.101.1.1preference60
#
user-interfacecon0
user-interfacevty04
#
return
分部1配置脚本
#
sysnameBranch1
#
ikelocal-namebranch1 /分部1的ike的local-name为:
branch1/
#
radiusschemesystem
#
domainsystem
#
ikepeercenter /配置到中心的ikepeer/
exchange-modeaggressive /设置IPSec为野蛮方式/
pre-shared-keyabc /预共享密钥为abc/
id-typename /选择名字作为ike协商过程中使用的ID/
remote-namecenter /对端的名字为center/
remote-address10.0.0.1 /对端的地址为10.0.0.1(中心的tunnel地址)/
#
ipsecproposal1 /定义ipsecproposal/
#
ipsecpolicybranch110isakmp /配置到中心的ipsecpolicy/
securityacl3001 /指定安全策略所引用的访问控制列表号/
ike-peercenter /引用ikepeer/
proposal1 /引用ipsecproposal/
#
aclnumber3001 /定义从分部1到中心的内网数据流/
rule0permitipsource192.168.2.00.0.0.255destination192.168.1.00.0.0.255
#
interfaceSerial2/0
link-protocolppp
ipaddress202.101.2.2255.255.255.252
#
interfaceTunnel0 /配置分部1和中心之间的GREtunnel/
ipaddress10.0.0.2255.255.255.252
source202.101.2.2
destination202.101.1.2
ipsecpolicybranch1 /在tunnel0上应用IPSecpolicybranch1/
#
interfaceNULL0
#
interfaceLoopBack0
ipaddress2.2.2.2255.255.255.255
#
interfaceEthernet0/0 /配置分部1的内网地址/
ipaddress192.168.2.1255.255.255.0
#
ospf1
area0.0.0.10 /分部1属于area10/
network2.2.2.20.0.0.0
network10.0.0.00.0.0.3
network192.168.2.00.0.0.255
#
iproute-static0.0.0.00.0.0.0202.101.2.1preference60
#
user-interfacecon0
user-interfacevty04
#
return
分部2配置脚本
#
sysnameBranch2
#
ikelocal-namebranch1 /分部2的ike的local-name为:
branch2/
#
radiusschemesystem
#
domainsystem
#
ikepeercenter /配置到中心的ikepeer/
exchange-modeaggressive /设置IPSec为野蛮方式/
pre-shared-keyabc /预共享密钥为abc/
id-typename /选择名字作为ike协商过程中使用的ID/
remote-namecenter /对端的名字为center/
remote-address10.0.0.5 /对端的地址为10.0.0.5(中心的tunnel地址)/
#
ipsecproposal1 /定义ipsecproposal/
#
ipsecpolicybranch110isakmp /配置到中心的ipsecpolicy/
securityacl3001 /指定安全策略所引用的访问控制列表号/
ike-peercenter /引用ikepeer/
proposal1 /引用ipsecproposal/
#
aclnumber3001 /定义从分部2到中心的GRE数据流/
rule0permitipsource192.168.3.00.0.0.255destination192.168.1.00.0.0.255
#
interfaceSerial2/0
link-protocolppp
ipaddress202.101.3.2255.255.255.252
#
interfaceTunnel0 /配置分部1和中心之间的GREtunnel/
ipaddress10.0.0.6255.255.255.252
source202.101.3.2
destination202.101.1.2
ipsecpolicybranch2 /在tunnel0上应用IPSecpolicybranch2/
#
interfaceNULL0
#
interfaceLoopBack0
ipaddress3.3.3.3255.255.255.255
#
interfaceEthernet0/0 /配置分部1的内网地址/
ipaddress192.168.3.1255.255.255.0
#
ospf1
area0.0.0.20 /分部2属于area20/
network3.3.3.30.0.0.0
network10.0.0.40.0.0.3
network192.168.3.00.0.0.255
#
iproute-static0.0.0.00.0.0.0202.101.3.1preference60
#
user-interfacecon0
user-interfacevty04
#
return
【验证】
1、中心上的ikesa状态:
dispikesa
connection-id peer flag phase doi
----------------------------------------------------------
44 10.0.0.2 RD 1 IPSEC
48 10.0.0.6 RD 2 IPSEC
47 10.0.0.6 RD 1 IPSEC
45 10.0.0.2 RD 2 IPSEC
flagmeaning
RD--READYST--STAYALIVERL--REPLACEDFD--FADINGTO—TIMEOUT
2、中心上的IPSecsa状态:
dispipsecsa
===============================
Interface:
Tunnel0
pathMTU:
64000
===============================
-----------------------------
IPsecpolicyname:
"branch1"
sequencenumber:
10
mode:
isakmp
-----------------------------
connectionid:
8
encapsulationmode:
tunnel
perfectforwardsecrecy:
None
tunnel:
local address:
10.0.0.1
remoteaddress:
10.0.0.2
flow:
(4timesmatched)
souraddr:
192.168.1.0/255.255.255.0 port:
0 protocol:
IP
destaddr:
192.168.2.0/255.255.255.0 port:
0 protocol:
IP
[inboundESPSAs]
spi:
2701983530(0xa10cff2a)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436664/2136
maxreceivedsequence-number:
2
udpencapsulationusedfornattraversal:
N
[outboundESPSAs]
spi:
2132567950(0x7f1c678e)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436632/2136
maxsentsequence-number:
3
udpencapsulationusedfornattraversal:
N
===============================
Interface:
Tunnel1
pathMTU:
64000
===============================
-----------------------------
IPsecpolicyname:
"branch2"
sequencenumber:
10
mode:
isakmp
-----------------------------
connectionid:
9
encapsulationmode:
tunnel
perfectforwardsecrecy:
None
tunnel:
local address:
10.0.0.5
remoteaddress:
10.0.0.6
flow:
(18timesmatched)
souraddr:
192.168.1.0/255.255.255.0 port:
0 protocol:
IP
destaddr:
192.168.3.0/255.255.255.0 port:
0 protocol:
IP
[inboundESPSAs]
spi:
1612204948(0x60184b94)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436188/2886
maxreceivedsequence-number:
9
udpencapsulationusedfornattraversal:
N
[outboundESPSAs]
spi:
3432409622(0xcc966a16)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436044/2886
maxsentsequence-number:
10
udpencapsulationusedfornattraversal:
N
3、中心路由表
dispiprout
RoutingTable:
publicnet
Destination/Mask ProtocolPre Cost Nexthop Interface
0.0.0.0/0 STATIC 60 0 202.101.1.1 Serial2/0/0
1.1.1.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0
2.2.2.2/32 OSPF 10 1563 10.0.0.2 Tunnel0
3.3.3.3/32 OSPF 10 1563 10.0.0.6 Tunnel1
10.0.0.0/30 DIRECT 0 0 10.0.0.1 Tunnel0
10.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0
10.0.0.4/30 DIRECT 0 0 10.0.0.5 Tunnel1
10.0.0.5/32 DIRECT 0 0 127.0.0.1 InLoopBack0
127.0.0.0/8 DIRECT 0 0 127.0.0.1 InLoopBack0
127.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0
192.168.1.0/24 DIRECT 0 0 192.168.1.1 LoopBack10
192.168.1.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0
192.168.2.0/24 OSPF 10 1563 10.0.0.2 Tunnel0
192.168.3.0/24 OSPF 10 1563 10.0.0.6 Tunnel1
202.101.1.0/30 DIRECT 0 0 202.101.1.2 Serial2/0/0
202.101.1.1/32 DIRECT 0 0 202.101.1.1 Serial2/0/0
202.101.1.2/32 DIRECT 0 0 127.0.0.1 InLoopBack0
4、分部1的ikesa状态:
dispikesa
connection-id peer flag phase doi
----------------------------------------------------------
27 10.0.0.1 RD|ST 1 IPSEC
28 10.0.0.1 RD|ST 2 IPSEC
flagmeaning
RD--READYST--STAYALIVERL--REPLACEDFD--FADINGTO—TIMEOUT
5、分部1的ipsecsa状态:
dispipsecsa
===============================
Interface:
Tunnel0
pathMTU:
64000
===============================
-----------------------------
IPsecpolicyname:
"branch1"
sequencenumber:
10
mode:
isakmp
-----------------------------
connectionid:
6
encapsulationmode:
tunnel
perfectforwardsecrecy:
None
tunnel:
local address:
10.0.0.2
remoteaddress:
10.0.0.1
flow:
(4timesmatched)
souraddr:
192.168.2.0/255.255.255.0 port:
0 protocol:
IP
destaddr:
192.168.1.0/255.255.255.0 port:
0 protocol:
IP
[inboundESPSAs]
spi:
2132567950(0x7f1c678e)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436664/2054
maxreceivedsequence-number:
2
udpencapsulationusedfornattraversal:
N
[outboundESPSAs]
spi:
2701983530(0xa10cff2a)
proposal:
ESP-ENCRYPT-DESESP-AUTH-MD5
saremainingkeyduration(bytes/sec):
1887436632/2054
maxsentsequence-number:
3
udpencapsulationusedfornattraversal:
N
6、分部1的路由表:
dispiprout
RoutingTable:
publicnet
Destination/Mask ProtocolPre Cost Nexthop Interface
0.0.0.0/0 STATIC 60 0 202.101.2.1 Serial2/0/0
1.1.1.1/32 OSPF 10 1563 10.0.0.1 Tunnel0
2.2.2.2/32 DIRECT 0 0 127.0.0.1 InLoopBack0
3.3.3.3/32 OSPF 10 3125 10.0.0.1 Tunnel0
10.0.0.0/30 DIRECT 0 0 10.0.0.2 Tunnel0
10.0.0.2/32 DIRECT 0 0 127.0.0.1 InLoopBack0
10.0.0.4/30 OSPF 10 3124 10.0.0.1 Tunnel0
127.0.0.0/8 DIRECT 0 0 127.0.0.1 InLoopBack0
127.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0
192.168.1.0/24 OSPF