思科路由器与华为路由器防火墙OSPF.docx
《思科路由器与华为路由器防火墙OSPF.docx》由会员分享,可在线阅读,更多相关《思科路由器与华为路由器防火墙OSPF.docx(6页珍藏版)》请在冰豆网上搜索。
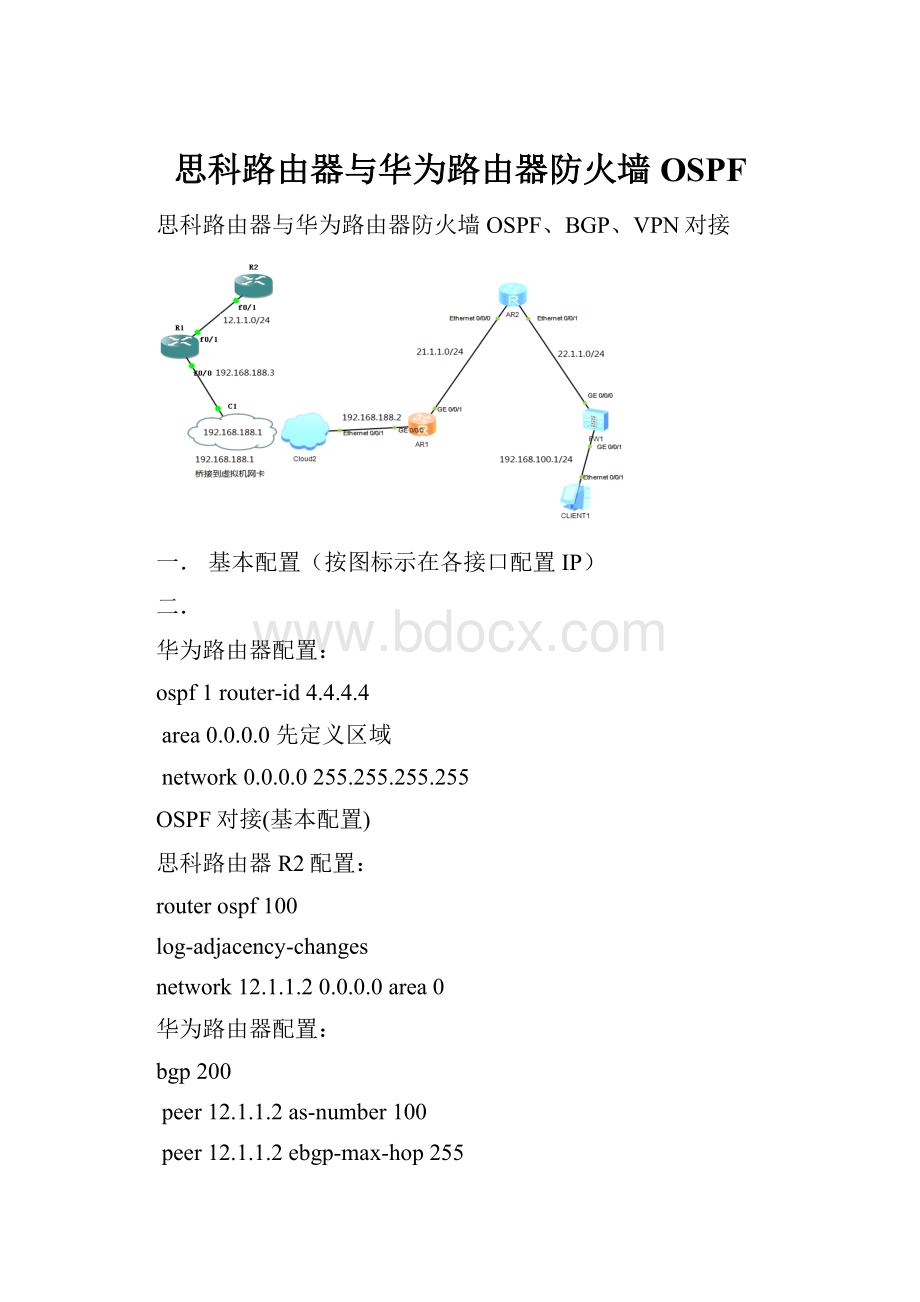
思科路由器与华为路由器防火墙OSPF
思科路由器与华为路由器防火墙OSPF、BGP、VPN对接
一.基本配置(按图标示在各接口配置IP)
二.
华为路由器配置:
ospf1router-id4.4.4.4
area0.0.0.0先定义区域
network0.0.0.0255.255.255.255
OSPF对接(基本配置)
思科路由器R2配置:
routerospf100
log-adjacency-changes
network12.1.1.20.0.0.0area0
华为路由器配置:
bgp200
peer12.1.1.2as-number100
peer12.1.1.2ebgp-max-hop255
ipv4-familyunicast
undosynchronization
network3.3.3.0255.255.255.0
peer12.1.1.2enable
#
三BGP对接(基本配置)
思科路由器配置:
routerbgp100
network2.2.2.0mask255.255.255.0
neighbor21.1.1.2remote-as200
neighbor21.1.1.2ebgp-multihop255
noauto-summary
四.Site-to-siteIPsecVPN
思科路由器配置:
cryptoisakmppolicy1
endes加密算法-des与对端一致
hashmd5哈希算法-md5与对端一致
authenticationpre-share认证方式-共享密钥与对端一致
group2密钥算法-保证密钥安全与对端一致
cryptoisakmpkey6try789address22.1.1.2设置共享密钥加密密码与对端一致
cryptoipsectransform-setccnpesp-3desesp-md5-hmacESP数据加密和哈希算法与对端一致
cryptomapccnp1ipsec-isakmp
setpeer22.1.1.2
settransform-setccnp
matchaddress100
ipnatinsidesourcelist120interfaceFastEthernet0/1overload
access-list100permitip192.168.200.00.0.0.255192.168.100.00.0.0.255定义VPN感趣流,
access-list120denyip192.168.200.00.0.0.255192.168.100.00.0.0.255排除VPN流量,不进行NAT
access-list120permitip192.168.200.00.0.0.255any
!
华为防火墙配置:
discurrent-configuration
aclnumber3000
rule5permitipsource192.168.100.00.0.0.255destination192.168.200.00.0.0.255定义VPN感兴趣流
ikeproposal100
endes
dhgroup2
authentication-algorithmmd5
saduration5000
#
ikepeercisco
pre-shared-keytry789
ike-proposal100
remote-address12.1.1.2
#
ipsecproposalcisco
espencryption-algorithm3des
#
ipsecpolicyto_c10isakmp
securityacl3000
ike-peercisco
proposalcisco
#
interfaceGigabitEthernet0/0/0
aliasGE0/MGMT
ipaddress22.1.1.2255.255.255.0
ipsecpolicyto_c
#
interfaceGigabitEthernet0/0/1
ipaddress192.168.100.1255.255.255.0
firewallzonetrust
setpriority85
addinterfaceGigabitEthernet0/0/1
#
firewallzoneuntrust
setpriority5
addinterfaceGigabitEthernet0/0/0
iproute-static0.0.0.00.0.0.022.1.1.1
#
policyinterzonelocaluntrustinbound
policy10
actionpermit
#
policyinterzonelocaluntrustoutbound
policy10
actionpermit
policysource22.1.1.20
#
policyinterzonetrustuntrustinbound
policy10
actionpermit
policysource192.168.200.0mask24
policydestination192.168.100.0mask24
#
policyinterzonetrustuntrustoutbound
policy10
actionpermit
policysource192.168.100.0mask24
#
nat-policyinterzonetrustuntrustoutboundnat-policy中policyno-nat在前,否则与ping不通对端的私有IP
policy0
actionno-nat
policysource192.168.100.00.0.0.255
policydestination192.168.200.00.0.0.255
policy1
actionsource-nat
policysource192.168.100.0mask24
easy-ipGigabitEthernet0/0/0
#
return
查看ikesaipsecsa
R2#shcryptoisakmpsa
dstsrcstateconn-idslotstatus
22.1.1.212.1.1.2QM_IDLE10020ACTIVE
disikesa
currentikesanumber:
2
-----------------------------------------------------------------------------
conn-idpeerflagphasevpn
-----------------------------------------------------------------------------
4000412.1.1.2RDv1:
2public
4000112.1.1.2RDv1:
1public
flagmeaning
RD--READYST--STAYALIVERL--REPLACEDFD--FADING
TO--TIMEOUTTD--DELETINGNEG--NEGOTIATINGD--DPD