205实验指导NATWord格式文档下载.docx
《205实验指导NATWord格式文档下载.docx》由会员分享,可在线阅读,更多相关《205实验指导NATWord格式文档下载.docx(27页珍藏版)》请在冰豆网上搜索。
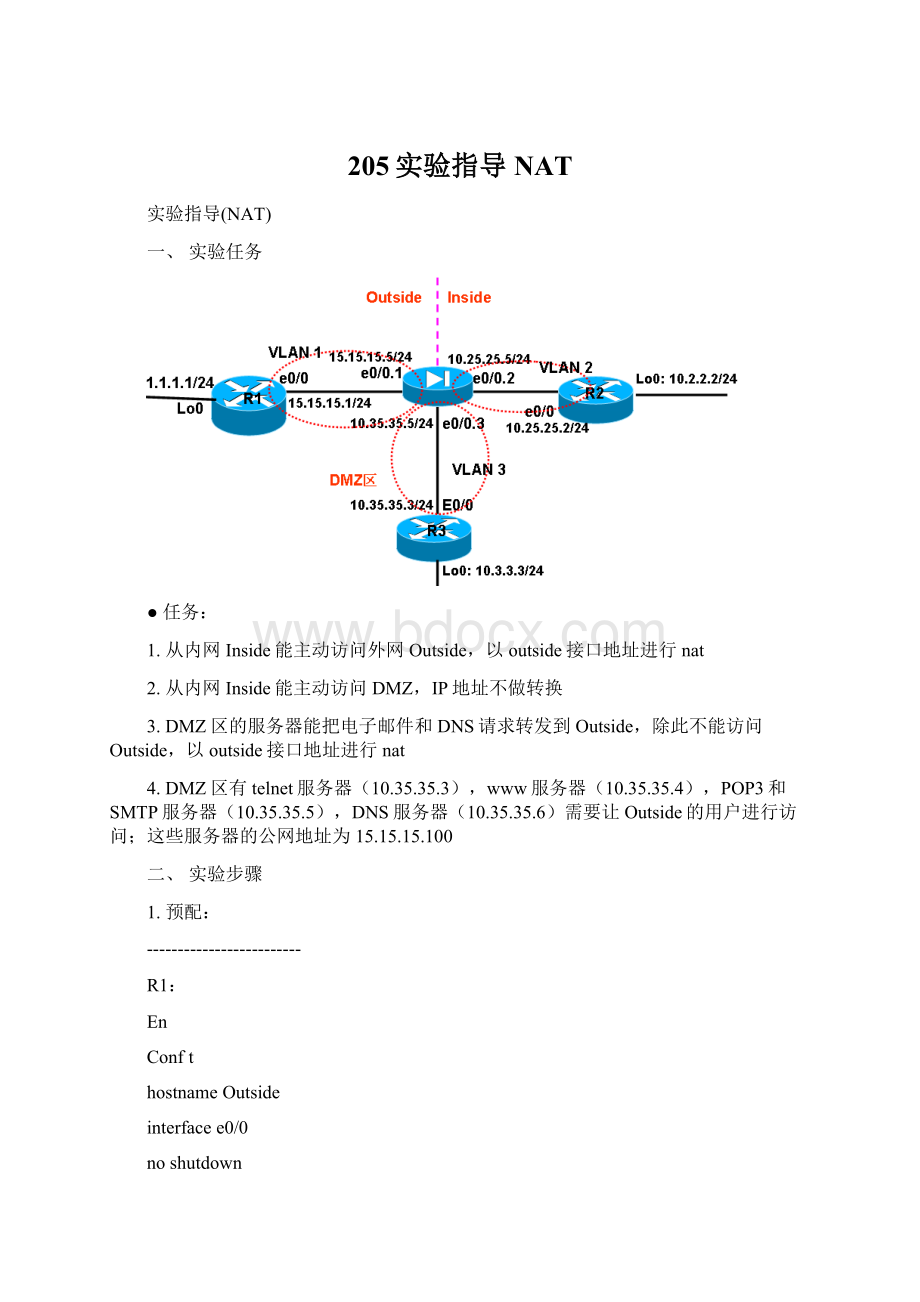
ipaddress1.1.1.1255.255.255.0
linevty04
passwordcisco
login
end
R2:
hostnameInside
ipaddress10.25.25.2255.255.255.0
ipaddress10.2.2.2255.255.255.0
routerrip
network10.0.0.0
R3:
hostnameDMZ
ipaddress10.35.35.3255.255.255.0
ipaddress10.3.3.3255.255.255.0
S1:
(在“#”下执行以下命令)
vlandatabase
vlan2
vlan3
exit
conft
hostnameSwitch
interfaceFastEthernet0/0
shutdown
interfaceFastEthernet0/5
noshutdown
switchporttrunknativevlan1000
switchporttrunkendot
switchportmodetrunk
duplexfull
speed10
interfaceFastEthernet0/2
switchportmodeaccess
switchportaccessvlan2
interfaceFastEthernet0/3
switchportaccessvlan3
2.基本配置(PIX上):
pixfirewall(config)#hostnameFireWall
FireWall(config)#interfaceEthernet0
FireWall(config-if)#noshutdown
FireWall(config)#interfaceEthernet0.1
FireWall(config-subif)#vlan1
FireWall(config-subif)#nameifOutside
FireWall(config-subif)#ipaddress15.15.15.5255.255.255.0
FireWall(config)#interfaceEthernet0.2
FireWall(config-subif)#vlan2
FireWall(config-subif)#nameifInside
FireWall(config-subif)#ipaddress10.25.25.5255.255.255.0
FireWall(config)#interfaceEthernet0.3
FireWall(config-subif)#vlan3
FireWall(config-subif)#nameifDMZ
FireWall(config-subif)#ipaddress10.35.35.5255.255.255.0
FireWall(config-subif)#routeoutside0015.15.15.1
FireWall(config)#routerrip
FireWall(config-router)#network10.0.0.0
FireWall(config-router)#redistributestatic
FireWall(config-subif)#security-level0
FireWall(config-)#interfaceEthernet0.2
FireWall(config-subif)#security-level100
FireWall(config-subif)#security-level50
测试:
从R2和R3telnet1.1.1.1,检测没有进行NAT前防火墙的工作情况
3.配置Inside和DMZ区访问外网的PAT:
FireWall(config)#nat-control
FireWall(config)#nat(inside)110.0.0.0255.0.0.0
FireWall(config)#nat(dmz)110.0.0.0255.0.0.0
FireWall(config)#global(outside)1interface
从R2和R3telnet1.1.1.1,查看是以什么地址连接到R1的?
R2#telnet1.1.1.1
Trying1.1.1.1...Open
UserAccessVerification
Password:
R1>
showusers
LineUserHost(s)IdleLocation
0con0idle00:
04:
58
*130vty0idle00:
00:
0015.15.15.5
131vty1idle00:
0115.15.15.5
在PIX上,查看连接和转换项:
PIX1(config)#showxlate
2inuse,2mostused
PATGlobal15.15.15.5(1025)Local10.35.35.3(42895)
PATGlobal15.15.15.5(1024)Local10.25.25.2(51483)
PIX1(config)#showconn
6inuse,6mostused
TCPout1.1.1.1:
23in10.35.35.3:
42895idle0:
18bytes102flagsUIO
23in10.25.25.2:
51483idle0:
06bytes482flagsUIO
4.限制DMZ的服务器只能转发电子邮件和DNS到Internet(PIX上):
FireWall(config)#access-listDMZ_INextendedpermittcpanyanyeqsmtp
FireWall(config)#access-listDMZ_INextendedpermittcpanyanyeqpop3
FireWall(config)#access-listDMZ_INextendedpermittcpanyanyeqdomain
FireWall(config)#access-listDMZ_INextendedpermitudpanyanyeqdomain
FireWall(config)#access-groupDMZ_INininterfaceDMZ
测试能否从R3telnet1.1.1.1(R1)?
5.配置Inside访问DMZ区NAT0(PIX上):
FireWall(config)#access-listNONATextendedpermitip10.0.0.0255.0.0.010.0.0.0255.0.0.0
FireWall(config)#nat(Inside)0access-listNONAT
从R2telnetR3(10.3.3.3),查看是以什么地址连接到R3的?
R2#telnet10.3.3.3
Trying10.3.3.3...Open
R3>
showuser
02:
36
0010.25.25.2
0inuse,2mostused
5inuse,6mostused
TCPout10.3.3.3:
37873idle0:
09bytes90flagsUIO
//注:
“nat0+ACL”是没有xlate项的,这和“nat0”是不一样的
6.配置Outside访问DMZ区上的服务器—静态NAT(PIX上):
FireWall(config)#access-listOUTSIDE_INextendedpermittcpanyhost15.15.15.100eqtelnet
FireWall(config)#access-listOUTSIDE_INextendedpermittcpanyhost15.15.15.100eqwww
FireWall(config)#access-listOUTSIDE_INextendedpermittcpanyhost15.15.15.100eqpop3
FireWall(config)#access-listOUTSIDE_INextendedpermittcpanyhost15.15.15.100eqsmtp
FireWall(config)#access-listOUTSIDE_INextendedpermitudpanyhost15.15.15.100eqdomain
FireWall(config)#access-listOUTSIDE_INextendedpermittcpanyhost15.15.15.100eqdomain
FireWall(config)#access-groupOUTSIDE_INininterfaceOutside
FireWall(config)#static(DMZ,Outside)tcp15.15.15.100telnet10.35.35.3telnetnetmask255.255.255.255
FireWall(config)#static(DMZ,Outside)tcp15.15.15.100www10.35.35.4wwwnetmask255.255.255.255
FireWall(config)#static(DMZ,Outside)tcp15.15.15.100pop310.35.35.5pop3netmask255.255.255.255
FireWall(config)#static(DMZ,Outside)tcp15.15.15.100smtp10.35.35.5smtpnetmask255.255.255.255
FireWall(config)#static(DMZ,Outside)udp15.15.15.100domain10.35.35.6domainnetmask255.255.255.255
FireWall(config)#static(DMZ,Outside)tcp15.15.15.100domain10.35.35.6domainnetmask255.255.255.255
从R1telnetR3(15.15.15.100是其公网地址),查看是以什么地址连接到R3的?
R1#15.15.15.100
Trying15.15.15.100...Open
01:
00
0015.15.15.1
5inuse,5mostused
PATGlobal15.15.15.100(23)Local10.35.35.3(23)
PATGlobal15.15.15.100(80)Local10.35.35.4(80)
PATGlobal15.15.15.100(110)Local10.35.35.5(110)
PATGlobal15.15.15.100(25)Local10.35.35.5(25)
PATGlobal15.15.15.100(53)Local10.35.35.6(53)
三、完整配置
-----------------------------R1------------------------
!
version12.4
servicetimestampsdebugdatetimemsec
servicetimestampslogdatetimemsec
noservicepassword-encryption
hostnameR1
boot-start-marker
boot-end-marker
noaaanew-model
memory-sizeiomem5
ipcef
interfaceLoopback0
ipaddress1.1.1.1255.255.255.0
interfaceEthernet0/0
full-duplex
interfaceEthernet0/1
noipaddress
half-duplex
interfaceEthernet0/2
interfaceEthernet0/3
interfaceSerial1/0
serialrestart-delay0
interfaceSerial1/1
interfaceSerial1/2
interfaceSerial1/3
iphttpserver
noiphttpsecure-server
iproute10.0.0.0255.0.0.015.15.15.5
control-plane
linecon0
lineaux0
End
-----------------------------R2------------------------
hostnameR2
ipaddress10.2.2.2255.255.255.0
-----------------------------R3------------------------
hostnameR3
ipaddress10.3.3.3255.255.255.0
noi